Describe the Uses for Ieee 802.1 X Access Control
IEEE 8021X is an IEEE Institute of Electrical and Electronics Engineers standard for port-based network access control. The IEEE 8021X standard Port-based Network Access Control defines a mechanism for port-based network access control that makes use of the physical access characteristics of IEEE 802 LAN infrastructure.

Using The 802 1x Standard To Secure Nextgen Multimedia Voip Phones Embedded Com
8021X is used for secure network authentication.

. If you are an organization dealing with valuable and sensitive information you need a secure method of transporting data. Revision of IEEE Std 8021X-2001 Port-based network access control makes use of the physical access characteristics of IEEE 802 Local Area Networks LAN infrastructures in order to provide a means of authenticating and authorizing devices attached to a LAN port that has point-to-point connection characteristics and of preventing access to that port in cases in. Defines characteristics operating.
It defines standards and protocols for wired local area networks WLAN metropolitan area networks MAN and wireless networks. A functional unit that interconnects two or more IEEE 802 networks that use the same data link layer DLL protocols above the medium access control MAC sublayer butcan use different MAC protocols. This port-based network access control uses the physical characteristics of the switched Local Area Network LAN infrastructure to authenticate devices attached to a LAN port.
8021AB - Station and Media Access Control Connectivity Discovery. Its main purpose is to provide an authentication mechanism for devices and users attempting to connect to wired and wireless LANs so. The MAC sublayer of the IEEE 802 RM exists between the PHY and the LLC sublayer to provide a service for the LLC sublayer.
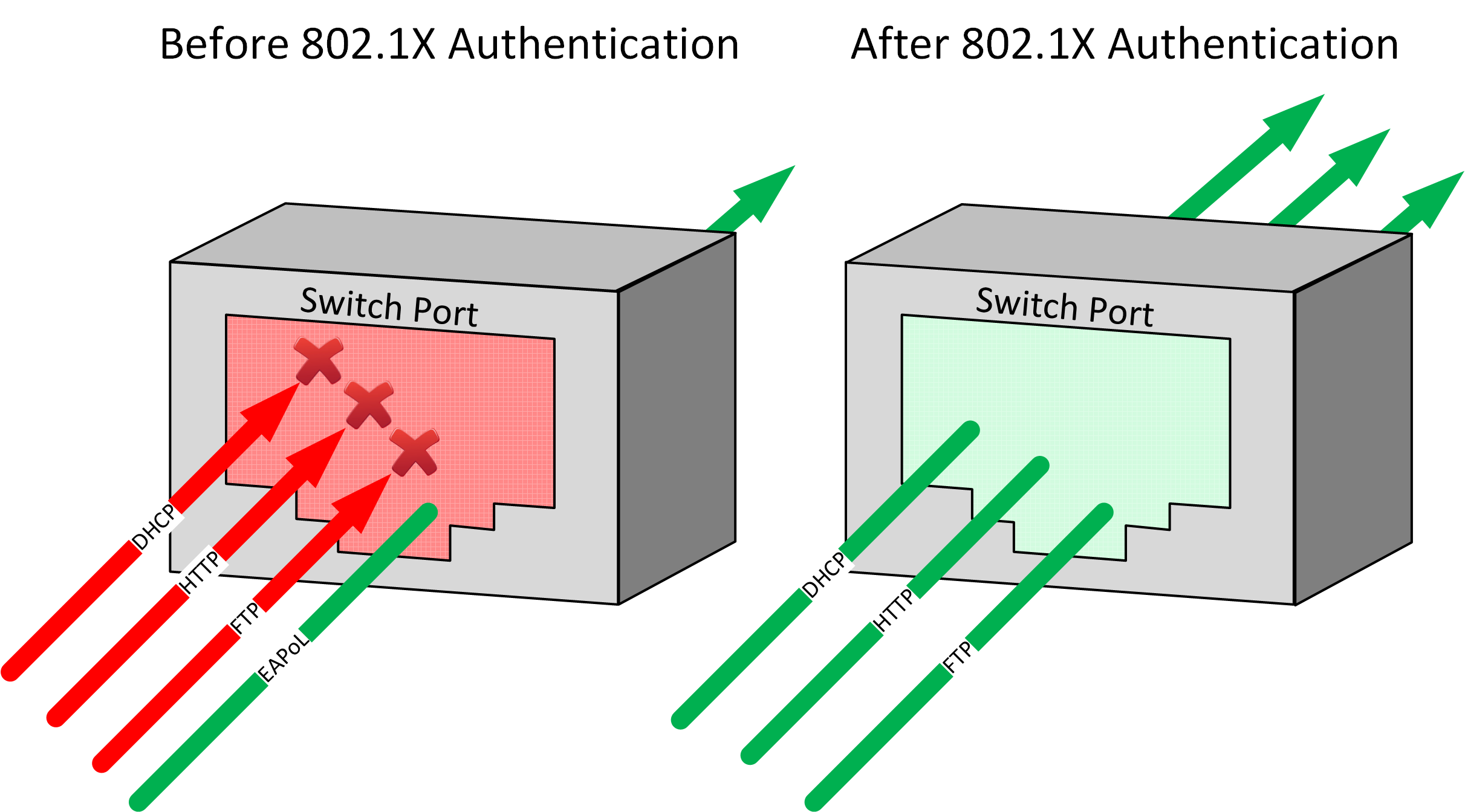
Port-based network access control regulates access to the network guarding against transmission and reception by unidentified or unauthorized parties and consequent network disruption theft of service or data loss. These Application Notes describe the configuration of Cisco 8021x Multi-domain Authentication MDA on a Cisco Catalyst 3750 with Avaya 9620 9630 4621SW and 4610SW IP Telephones. Protocols that configure manage and regulate access to these networks and.
8021X-REV - Revision of 8021X-2004 - Port Based Network Access Control. User authentication is necessary for identity based access control and 8021X clearly promises to meet this need. Smart Card or Certificate also displayed but grayed-out in a drop-down box.
An IEEE standard for network access control. Hence you can use an 8021X port with port security enabled to limit the number or group of clients that can access the network. 8021X defines a framework that can be used to should be able to EAP see 5 is a protocol for transporting perform access control but leaves unsolved the authentication methods.
It offers a framework in problem of how to move credentials from one play the role of which many different authentication methods authenticator to another to avoid the repetition certificate-based. Port-based network access control. IEEE Standard for Local and metropolitan area networksPort-Based Network Access Control.
IEEE 802 LANs are deployed in networks that convey or provide access to critical data that support mission critical applications or that charge for service. The IEEE 8021x standard defines a client-server-based access control and authentication protocol that restricts unauthorized clients from connecting to. IEEE 8021X ensures a user authentication framework where network access is denied upon failed authentication.
Port-based network access control allows a network administrator to restrict the use of IEEE 802 LAN service access points ports to secure communication between authenticated and authorized devices. This standard specifies a common architecture functional elements and. The IEEE 8021X standard defines the port-based network access control that is used to provide authenticated wired access to Ethernet networks.
Formally known as the IEEE Standard for Local and metropolitan area networks. The ability to verify the identity of a user or computer system on a computer network. 8021X has been around for a number of years and has been proposed as the user authentication solution for both wired and wireless LANs.
Not to be confused with 80211x which is the term used to describe the family of 80211 standards for wireless LAN technology 8021X is the IEEE standard for port-based Network Access Control for enabling restricted use of IEEE 802 LAN service access points ports to secure communication between authenticated and authorized devices. When WPA-PSK with TKIP data encryption is enabled in the Wizard T-mobile ROM 216102WWE and I click on the 8021x tab a page displays showing a box checked by default which cannot be unchecked to Use IEEE 8021x network access control and with EAP type. The MAC sublayer of the IEEE 802 RM exists between the PHY and the LLC sublayer to provide a service for the LLC sublayer.
8021X is used so devices can communicate securely with. IEEE 8021X controls access to wireless or virtual local area networks VLAN and applies traffic policies based on user identity and credentials. Used predominantly in Wi-Fi wireless networks 8021X keeps the network port disconnected until authentication is completed.
Is an IEEE Standard for port-based Network Access Control PNAC. Data frames are transmitted and received using the MAC Service specified in IEEE Std 8021AC. Port-Based Network Access Control.
It provides a means of authenticating and authorizing devices attached to a LAN port that has point-to-point connection characteristics. When you enable port security and 8021X on a port 8021X authenticates the port and port security manages the number of MAC addresses allowed on that port including that of the client. It provides an authentication mechanism to devices wishing to attach to a LAN or WLAN.
IEEE 8021X adheres to IEEE 80211 protocols to enhance wireless network security. It is part of the IEEE 8021 group of networking protocols. This document defines a protocol and a set of managed objects that can be used for discovering the physical topology and connection end-point information from adjacent devices in 802 LANs and MANs.
A functional unit that interconnects two or more IEEE 802 networks that use the same data link layer DLL protocols above the medium access control MAC sublayer but can use different MAC protocols. IEEE 802 is an Institute of Electrical and Electronics Engineers IEEE standard set that covers the physical and data link layers of the Open Systems Interconnection OSI model. The protocol is not restricted from running on non-802 media.

Configure Windows 10 For 802 1x User Authentication Virtualization Howto
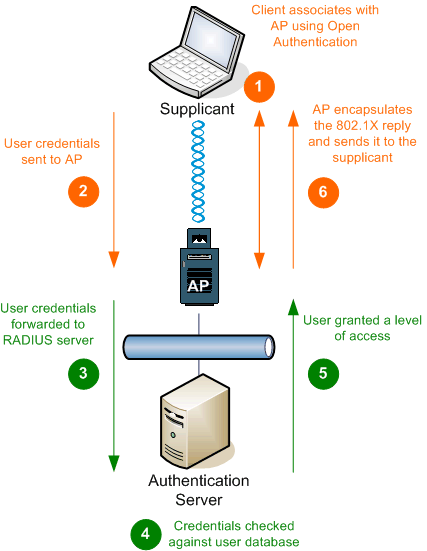
802 1x Extensible Authentication Protocol Flexible Authentication Via Secure Tunnelling

Powerlink Ap2403 802 11b G N 7in1 Mini Wireless Travel Ap Router By Powerlink 29 99 Description The Powerlink Ap2403 Wireless Router Wireless Routers Router
How To Use An Ethernet Connection Protected By 802 1x To Make A Hotspot In Mac Osx Quora

Configuring Ieee 802 1x Authentication Settings Canon Imageclass Mf746cdw Mf745cdw Mf743cdw Mf741cdw Mf644cdw Mf642cdw Mf641cw User S Guide
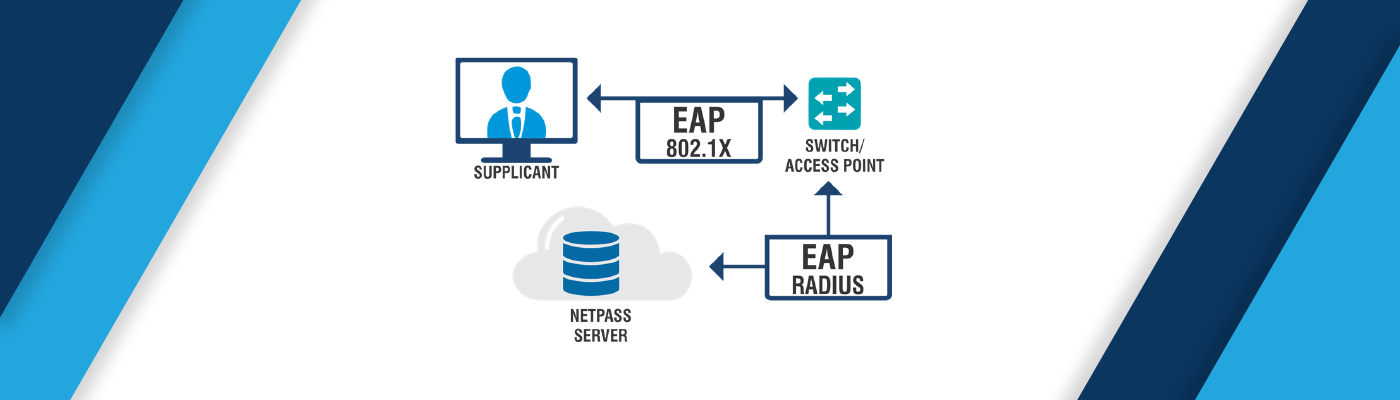
Configuring Ieee 802 1x Port Based Authentication Zencc

Snom 370 Voip Phone Offering 12 Lines Poe Large Display 12 Function Keys Voip Voip Phone Phone

Leviton 41108 Re8 Voice Grade Quickport Connector Black By Leviton 8 32 From The Manufacturer Patch Panels Structured Cabling Computer Accessories

Leviton 41108 Re8 Voice Grade Quickport Connector Black By Leviton 8 32 From The Manufacturer Patch Panels Structured Cabling Computer Accessories
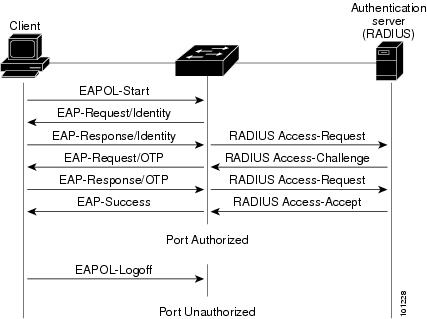
Cisco Content Hub Configuring Ieee 802 1x Port Based Authentication

802 1x Authentication For Wifi Networks The Benefits Purple
Chapter 4 802 1x Eap Authentication
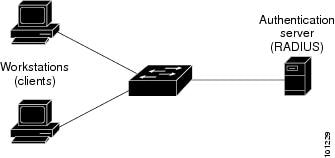
Cisco Content Hub Configuring Ieee 802 1x Port Based Authentication

Notes About 802 1x And Mac Authentication Vcloudnine De

802 1x Extensible Authentication Protocol Flexible Authentication Via Secure Tunnelling
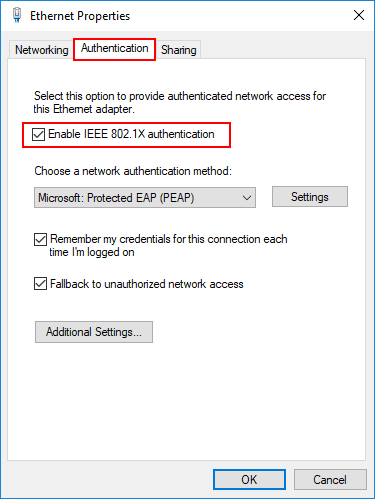
Configure Windows 10 For 802 1x User Authentication Virtualization Howto
Comments
Post a Comment